As we are more than halfway through the year, we have seen that the Covid Pandemic has accelerated the need of many companies to provide a better remote access solution not just for sales, but for many other divisions. Although many have been concerned with performance of their applications with this new setup, many are also starting to see the need to improve their security for these solutions as well.

A global study was done by Cybersecurity Insiders which showed that many are already looking into incorporating it into their Secure Access Architecture. Below are a few key findings from the study:
- Over 60% of participating organizations find the Zero Trust tenets of continuous authentication and authorization, trust earned through entity verification, and data protection as most compelling for their organization
- Over 40% of participating organizations expressed privilege management, insecure partner access, cyberattacks, shadow IT risks, and vulnerable mobile and at-risk device resource access as top challenges to secure access to applications and resources
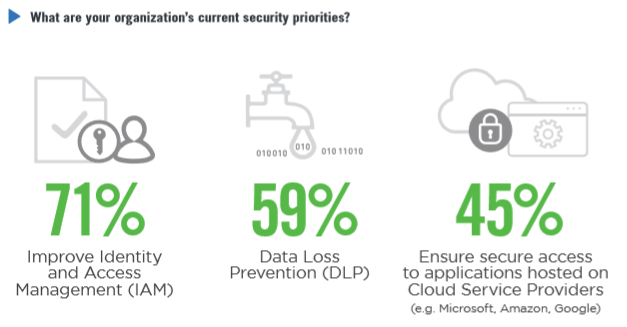
- 45% of participating organizations are concerned with public cloud application access security, and 43% with BYOD exposures
- 70% of organizations plan to advance their identity and access management capabilities
- 30% of organizations are seeking to simplify secure access delivery including enhancing user experience and optimizing administration and provisioning
- 41% of participating organizations are looking to re-evaluate their secure access infrastructure and consider Software Defined Perimeter (SDP) – with the majority requiring a hybrid IT deployment and a quarter adopting a SaaS implementation.
On a global scale, we can see that the trend of remote access solutions is becoming the new norm for many organizations. While we move forward, our IT Security team has to deal with the increased security risks as we open new security flaws with unauthorized and non-compliant devices.
This is where security vendors with Zero Trust Security products and solution providers like us can help your organization. We have been helping many clients throughout the lockdown to find the right solution for them whether it has been for improving remote access performance or security.

The Zero Trust Model can be summarized by the following questions: Can the user prove their identity and of the device they are using? Are they allowed to access this application? Is the network they are using secure? If they cannot answer yes to either of these questions, they should not gain access to the network.
If you are interested to learn more about the solution, you may read more here, or you may contact us directly at 88939515 for us to better assess your situation and find the right solution for you!

