Email has been a staple use of communication ever since it was introduced. Businesses are constantly trying to keep their email security updated to avoid attacks and data leaks. However, attacks like phishing are constantly evolving to evade email security technology. From attacks that try to fool users into clicking links to emails exploiting vulnerabilities, attackers are mixing or combining them to better succeed in getting into your network. This is why it is important to not only update your security, but to also educate your users.
Below are a few of these methods that are being used in the online environment that you and your users should be aware of:
Favicon Evasion

The first Phishing evasion method affects the icon of the browser tab called the favicon. If you look carefully at some links that ask you to login to your account, there are some inconsistencies. The left image and right image are similar but have major differences. This is purposely done to evade detection from email security, the left image has different color patterns then the actual Microsoft logo.
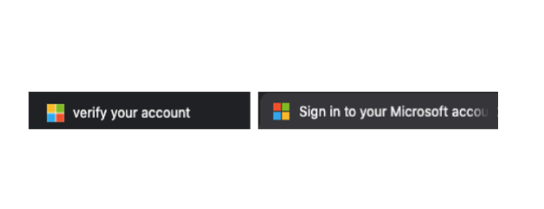
Logo Evasion

They also apply small differences on the logos they use on the login link. The left image uses a similar font and is in bold. This is to cause errors in template matching and increase the chance of being missed in Phising detection engines similar to the Favicon Evasion method

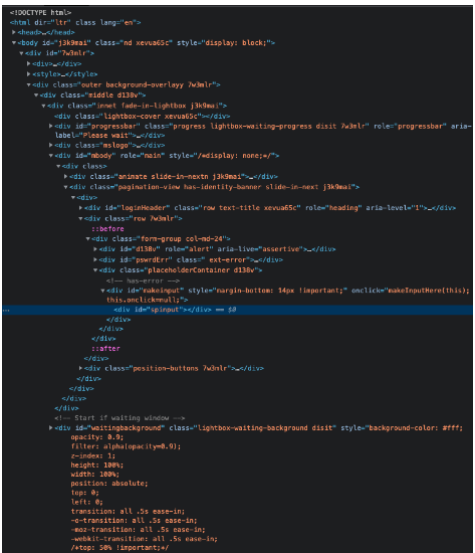
Form Evasion

When looking at the inside of the sign-in link (the HTML code), we might see some things that look suspicious. Some detection engines are looking for form codes, so what attackers do is use <div> tags instead to look exactly the same.
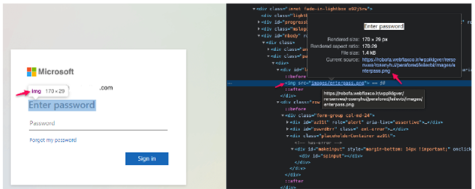
Suspicious Text in Images

Some detection engines scan for fields that asks for a user’s password, like “enter password”. This is then investigated if this is a legitimate site. How attackers try to bypass this, they use a text image of “enter password” to evade this.
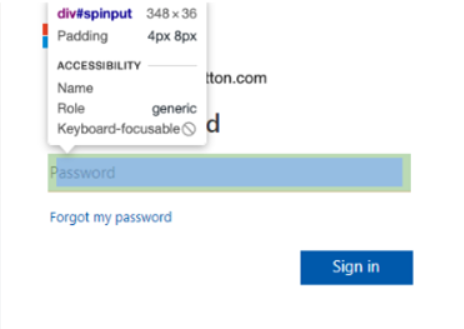
Input Field in Disguise

Another technique that phishing detection engines may use is scanning the HTML for input fields, indicating that this might be a credential theft attempt. In this attack, attackers hide an input field by creating an empty div with a background image showing the word password. This is another way attackers evade detection from email security solutions.
To learn more on email security methods or if you would like to better educate your users, you can consult with us by sending us an email at marketing@ctlink.com.ph!

