Does your business have enough bandwidth?
Many businesses today are looking for ways to upgrade their current bandwidth because of user feedback, they complain mostly about slow browsing speeds. Little do they know that there is a certain user in the office that is “torrenting” on the network, which results to bandwidth hogging and can even put the business at risk.
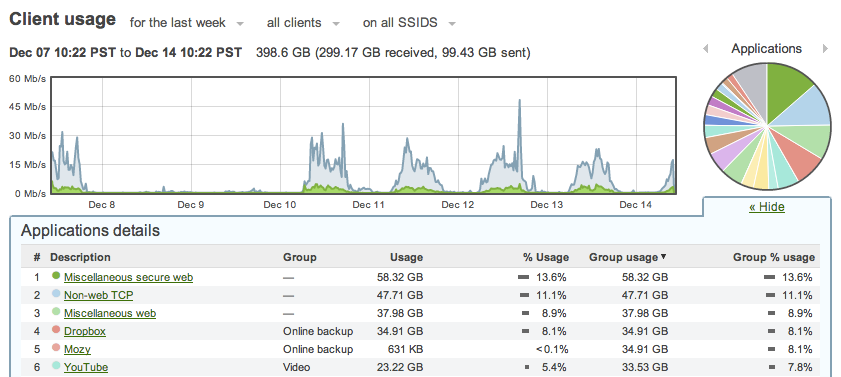
However, administrators can now feel reassured with Cisco Meraki’s Layer 7 application fingerprinting which gives them a better view of their network. Network administrators/managers can rely on this level of visibility every day to see beyond the size and rate of data transfers on their networks and gain insight into the actual behavior of their users. It’s useful to see patterns in large spikes of traffic on the network, but it’s even better to know whether those spikes are coming from online backup or from BitTorrent.
What’s better than traffic Visibility? Traffic shaping!
So now the administrators have identified which applications (and most importantly, which users) are using more bandwidth than necessary, what can you do about it?
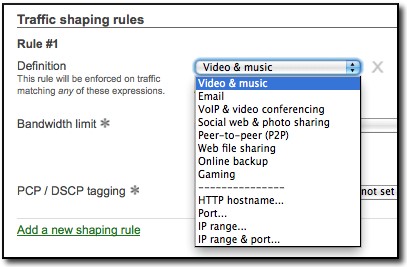
You can now create application-specific shaping policies for total control over your wired and wireless network. With the built-in Traffic Shaper in Cisco Meraki, shaping policies can be created that apply per user bandwidth limits for specific applications such as video streaming sites, as well as apply QoS (Quality of Service) priority levels at both Layer 2 and 3 to make sure your critical traffic gets prioritized across the network.
The Cisco Meraki portfolio includes wireless access points, switches, security appliances, and mobile device management solutions. What sets Cisco Meraki apart is that all of these are centrally managed from the cloud. This makes them significantly easier to deploy and manage than traditional networks.
Contact us at 893-9515 to try Cisco Meraki for yourself and discover the power of cloud networking today!
