Service Framework for the Implementation of Endpoint Security
Endpoint security has grown beyond traditional antivirus programs, now offering a full range of IT protection, including intrusion prevention, endpoint encryption, virtual patching, and email security. With cyber threats, such as phishing attacks, on the rise—especially with a reported 200% increase during the 2020 lockdown—protecting endpoints is more important than ever.
However, integrating an endpoint security solution is not always straightforward. That’s where we come in. Our team at CT Link uses a proven implementation framework to simplify the process, helping your organization secure its endpoints efficiently and effectively. From planning to deployment, we ensure your endpoint security measures are fully integrated and optimized to meet your specific needs.
Endpoint Security Service Framework
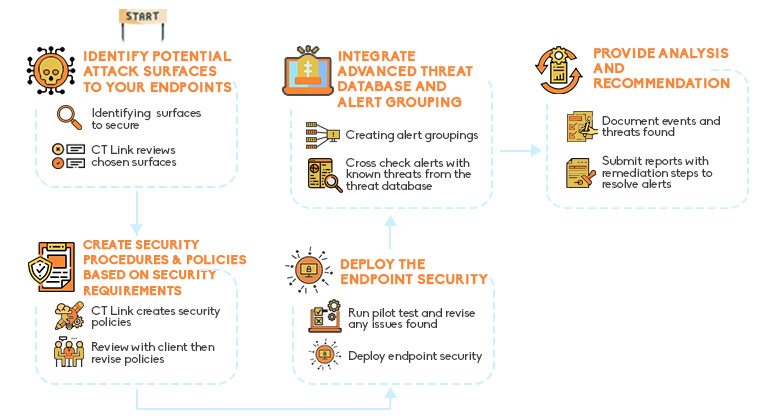

Identify potential attack surfaces to your endpoints
Endpoint security always starts with identifying and defining critical areas and data that are crucial to your business. This will act as the foundation on which we will design your endpoint security architecture. We closely work with your IT Team to map out all areas of protection. This includes, but not limited to, emails, laptops, desktops, SaaS apps, IoT and OT devices.

Creating security procedures and policies based on your security requirements
The next step in our endpoint service would be creating the security policies based on the defined areas and data. Knowing where the sensitive data or places that can be vulnerable are, we can then strengthen and enforce better security. We assess your available resources and tailor your policies based on your requirements. This is to ensure that your security does not compromise your user’s experience.

Deploying the endpoint security
Our next step is to run a pilot test. This is to avoid any issues and misconfiguration during the migration step. Only when both CT Link and our client see no more issues in the pilot can we move to deployment. Depending on the number of endpoints, this can be the most time-consuming part of our service.

Advanced threat database and alert grouping
As your business grows, security priorities might change, or the number of alerts received may become overwhelming. We proactively adjust our solution during this stage. This is to avoid multiple false negative alerts your team has to handle. This is done through our solutions’ extensive threat database and analytic capabilities in which monitoring can be done daily through a cloud dashboard. Through it, we make sure that your security is always UpToDate and ready for emerging threats.

Comprehensive Analysis and Recommendations
Our team documents the events and threats that are found by our endpoint security solution. We submit reports to you in detail of what threats were found and their priority for resolution. This is to help guide your team efficiently resolve issues in the security. We also send our recommendations on how to better configure your network based on your security priorities as your business evolves.
If you are interested in learning more about our services, contact us by filling in the form here. We would be glad to go into further detail with your team by having one of our team members reach out!
By clicking “Submit,” you agree to our Privacy Policy and consent to the collection and use of your personal information as described therein.
