Security Tips: Different Business Email Compromise (BEC) Schemes to Watch Out For
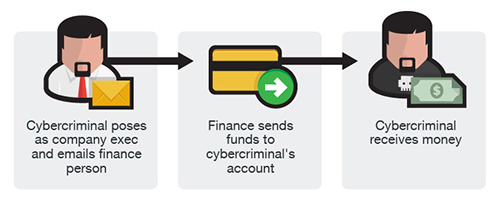
Business Email Compromise (BEC) Schemes In the past few years, millions of dollars have been lost to fraudsters and scammers. However, not all have been lost through malware attacks such as ransomware. Business email compromise (BEC) schemes are sophisticated attacks focused mostly on companies who do wireless transfers frequently. The FBI have estimated that nearly […]
CT Link Becomes a VMware Enterprise Partner!
On June 29, 2018, CT Link officially signed up to become a VMware enterprise partner. VMware’s core business focuses on support to modernize data centers, integrating public cloud, empowering digital workspaces and transforming security for its clients. These focuses have helped VMware become one of the leading figures in the virtualization software market and a main reason […]
Ransomware Lunch & Learn With Cisco!
Ransomware is becoming more prevalent now as more companies are starting to have their networks infected with these disruptive malware. With this in mind, Cisco has been improving their security portfolio to keep your IT infrastructure same from these malicious malware attacks. Learn more about it from our Cisco experts on July 17, 2018 at […]
Microsoft To-Do adds New Features Steps and List Sharing for its Users
It’s now been over a year since Microsoft has released To-Do, it’s intelligent task management app which was developed by the team behind wunderlist. With it being integrated with Office 365, the team has been collecting a multitude of feedback from users and have now released them in a couple of updates throughout this year. […]
Malware VPNFilter is on the Rise as Infected Routers Increase Globally
On May 24, a report was published by security researchers upon the discovery of a group who had infected more than 500,000 home and small-enterprise routers in at least 54 countries with their malware VPNFilter. This malware can attack, collect research, steal key credentials, monitor SCADA protocols, and install a kill command to destroy your device via your […]
Meraki Wireless Health is Now in Beta!
Last January Cisco announced that they would be adding an exciting new feature for Meraki, the Meraki Wireless Health. In essence, Wireless Health is a powerful heuristics engine which can promptly find errors which are affecting the end users experience across multiple stages of their connectivity, which includes association, authentication, IP addressing and DNS availability, […]
