A Closer look at Processor Vulnerabilities
The past few years has been rough on processor security, this especially for Intel as one of the biggest processor vulnerabilities Meltdown and Spectre was for nearly all their modern CPUs. Although patches came out almost immediately to solve these issues, this was just the start to the security vulnerabilities as other attacks such as […]
Keep your Data Safe Anywhere with Microsoft Azure Information Protection
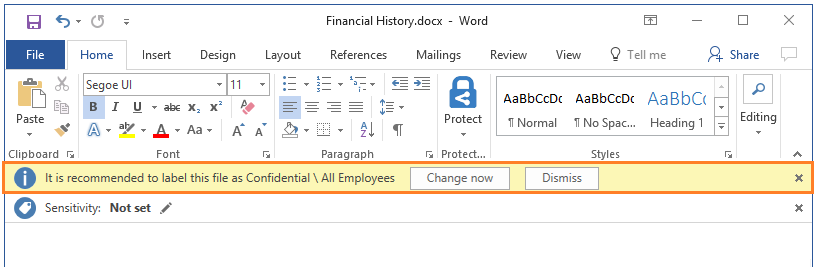
With the convenience of the internet and the evolving application market, company data is moving through different channels at a faster rate than possible before. This makes it easier for businesses to better serve the clients while also improving their operations. However, this also means that your data may be out there unprotected and used […]
Citrix Connect: A Closer look into Citrix SD-WAN for Business Critical Application
Looking to improve and secure connectivity and app performance for every location? In today’s digital age, businesses rely heavily on network connectivity and applications to keep their operations running smoothly. A delay or a failure in network connectivity or an application can cost a business time, money, and even customers. Therefore, it is crucial for […]
Data Protection: Looking Closer at Cloud Storage
The way we store data is evolving, from the days of punch cards, magnetic tape, discs, solid state, and flash we have now arrived to having what is called cloud storage. A research from IDC shows that IT Infrastructure sales into the cloud has finally surpassed traditional IT environments for the first time in the […]
Cisco Umbrella: Camuto Group Case Study
The Challenge A US footwear and lifestyle brand company, the Camuto Group, has been thriving in their industry due to the unique designs that sets them apart from the competition. However, the company’s creativity is also one of its IT’s main pain points when it comes to security. With almost 100 employees working remotely and […]
Security Vulnerabilities: A Closer Look at a Criminal’s View of your Business Systems
You may be hearing more and more these days of new security vulnerabilities being discovered in the news and may be wondering what exactly it may imply? Simply, a vulnerability represents the ideal opportunity for cyber criminals to infiltrate your system to compromise your data or to perform data theft. According to current data now, […]
