Cloud vs Edge Computing: Choosing the Right Approach for Your Business

Today, businesses operate in a diverse digital landscape where they can benefit from a variety of different technologies. A good example of this would be the topic of the article, cloud computing and edge computing. Both technologies can greatly help businesses improve on their operations depending on each business’ unique requirements or circumstances. Let’s delve […]
CT Link Systems, Inc. Returns to FEED: A Day of Tree Planting and Art Appreciation

In continuation of our commitment to environmental sustainability and community engagement, CT Link has once again visited on Fostering Education & Environment, Inc. (FEED) last April 20, 2024. Our team gathered early in the morning at our office for a special trip to Laguna to continue our tree-planting efforts from last year. Once we arrived […]
Public Advisory: Cash App Scam Using CT Link Name
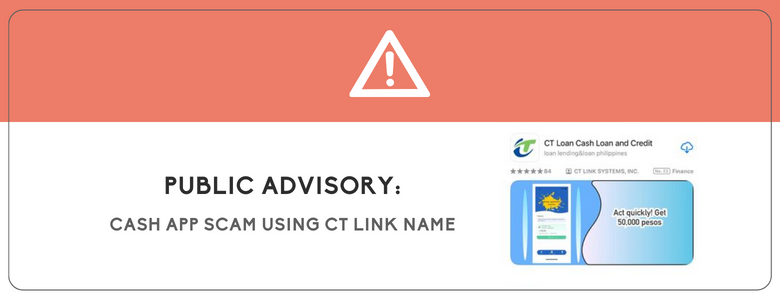
NOTICE TO THE PUBLIC Our company, CT Link Systems, Inc., is a leading IT solutions company based in the Philippines. Since 1998, our company has continuously nurtured its reputation as a provider of effective and cutting-edge technology solutions to top Philippine businesses. Recently, our company learned that an app called “CT Loan Cash Loan and Credit” is […]
Tech Companies in the Philippines: Driving Innovation and Growth in the Modern Business Landscape

In recent years, the tech industry in the Philippines has grown quickly, driven by improvements in digital technologies and a rising need for creative solutions in different areas. Tech companies in the Philippines are not just changing how businesses work; they are also playing a big role in boosting economic growth and creating new jobs. […]
Securing Access: Passwordless Biometric Authentication for Businesses

In today’s digital world, businesses are at risk of cyberattacks and data breaches more than ever before. Using just passwords to keep their valuable information safe isn’t enough anymore. That’s where passwordless authentication, such as biometric authentication, can become a good alternative. They provide a secure and easy way for users to log in without […]
Unlocking the Five Benefits of All-Flash with Pure Storage Solutions
In today’s digital world, businesses depend on data to innovate and stay ahead of the competition. All-flash storage solutions, like those from Pure Storage, have transformed the storage industry by offering five crucial benefits to businesses who implement it. To make the most of these benefits, businesses need help from Pure Storage resellers for smooth […]
