Preventing Data Breach From Unknown and Insider Threats in the Banking Sector
Many businesses run with the premise of customer data confidentiality. Data such as patient data, confidential documents from financial institutes and law firms are firmly secured to ensure the continuation of the business. This is why these businesses, especially in the banking industry, put heavy emphasis on keeping their data secure. However, threat actors know this and have taken different approaches to bypassing traditional security measures.
Below are a few ways that threat actors are now using to bypass security and infiltrate your infrastructure. These attacks can cause heavy losses to the business through compromised transactions and wide scale data breach:

Stolen Credentials
Threat actors know that most financial institutes are heavily guarded. So instead of trying to penetrate these defenses, they look for a backdoor entrance. The pandemic has seen a rise of attacks aimed at users of business whose security may not be as secure at home. Through phishing and other social engineered attacks, they are able to steal credentials and gain access to the business network through a legitimate account. This makes it harder to react to an attack and resolve it when you don’t even know it’s happening.

Insider Threats
Outside threats aren’t the only thing that can be detrimental to the financial industry. Whether it is intentional or not, users can also cause security threats. Users are less likely to be monitored and can have access to data that they are not responsible for. This can be harder to spot for your IT team when it comes to investigating fraudulent transactions or even sources of data breach.

Advanced Persistent Threats
Threat actors know that stealing from a financial institute can lead to a big pay day. This is why some threat actors are willing to invest in longer and harder to detect attacks towards them. Once these attacks infiltrate the network, they move laterally through your network slowly until they find what they need. They can even come out of it without being detected, making the organization unaware that they have been infiltrated and breached.
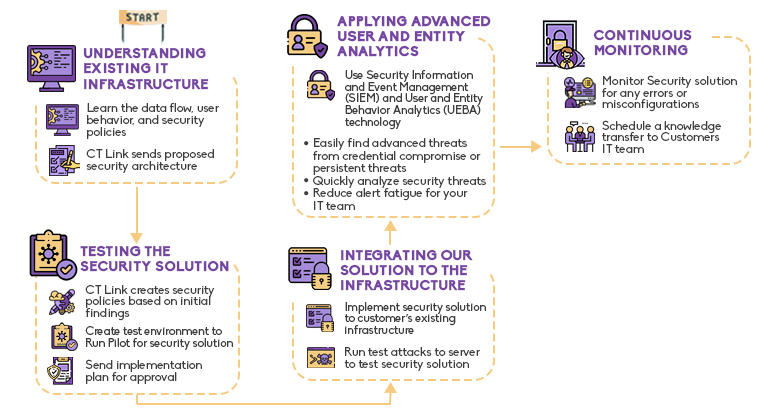
Advanced Event Management and Analytics as a Solution
The issues above may be concerning, however, there are solutions aimed to help minimize these threats. We at CT Link can help your business implement a security solution that uses Security Information and Event Management (SIEM) and User and Entity Behavior Analytics (UEBA) technology to help mitigate these threats.
A SIEM solution can collect events and logs from multiple security tools and critical systems. This alone already helps your team get all the necessary information to help find and understand attacks to your system. However, the amount of information can be overwhelming, and can cause alert fatigue to your team. This is where UEBA solutions can minimize the stress and increase the response time of dealing with threats.
UEBA solutions can help your team understand anomalous activities within your network and immediately alert your team to respond. It does this by analyzing a baseline of user and entity behavior within your network for normal behavior. Once something goes awry within the pattern, like when users are accessing sensitive data or using privileges they normally or shouldn’t be accessing in the first place. This is especially helpful in the age of IoT where many devices are being used to access business networks. Finding suspicious devices accessing the network at suspicious times and locations can be immediately blocked until allowed by your team.
These solutions specialize in monitoring your network events and can filter out alerts to lessen alert fatigue. Finding root causes of certain events and finding anomalous activity early are some few benefits of these solutions. Uncharacteristic behavior of users and endpoints can also be tracked and stopped before any theft or damage can be done to your data.
Contact us Today to learn more in-depth how SIEM and UEBA technology can bolster your security position!
By clicking “Submit,” you agree to our Privacy Policy and consent to the collection and use of your personal information as described therein.
