When Cisco announced the integration of Cisco Advanced Malware Protection with the Meraki MX last July, it was to provide a simple and effective way for MX customers to monitor, detect and remediate advanced threats. Now they are taking it a step further, they have now integrated their Threat Grid into the Meraki MX platform. This integration allows security teams to be able to better understand, prioritize and mitigate attacks by combining advanced sandboxing with threat intelligence.
With how advanced today’s malware and other advanced attacks are, it is harder for companies to just to rely on their first line of defenses. Even with some of the best security tools in place, it is still highly likely some of them will eventually get into your system. However, with Threat Grid, you can be able to avoid these situations. It rapidly analyzes files and suspicious behavior across your environment while providing your security team context-rich analytics. It also provides threat intelligence so your team will know what a file is doing or attempting to do which helps in quickly responding to the threats.
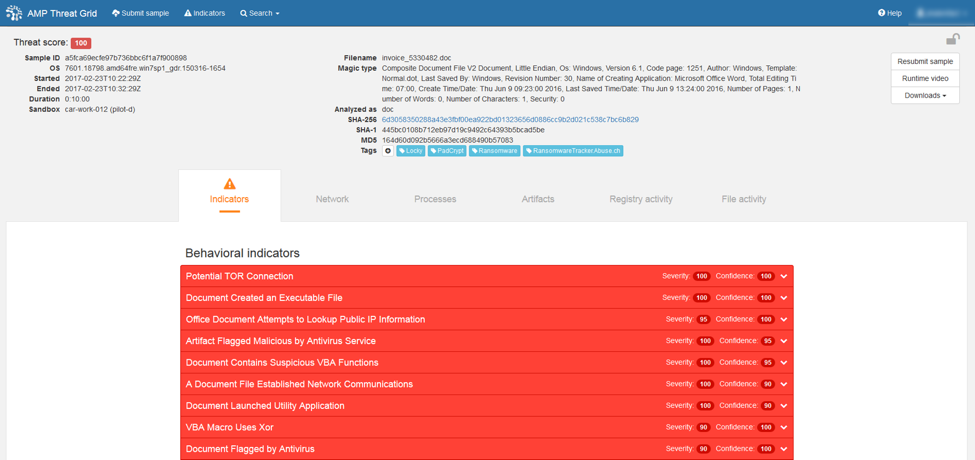
The integration starts with the AMP for Meraki integration. Files that pass through MX will be queried against AMP which will respond with a disposition of clean, malicious or unknown. The clean files are allowed through while malicious files are blocked and the unknown files are automatically sent to Threat Grid to be analyzed. After the analysis is complete, a detailed report and threat score will be displayed on the Meraki Security Center. Files with threat scores of 95 and higher are considered malicious which will trigger an alert as to notify the security team so they can remediate it ASAP.
Threat Grid for MX is available now as an add on to the MX Advanced Security license. Customers must have the Advanced Security License to purchase Threat Grid. To find out more contact us at 893-9515 and we will be happy to help!
